DAST Essentials quickstart
This quickstart steps you through running your first Dynamic Analysis using DAST Essentials.
You can use DAST Essentials to run an analysis of the following.
- Web applications
- REST APIs
You create a target that specifies the URL for the web application or API you want to analyze, then run the analysis from that target. DAST Essentials crawls the URL, scans all content, then analyzes the content to discover vulnerabilities. From within the target, you can monitor the analysis, review results, and configure settings and integrations.
Prerequisites
- You must have a user account in the Commercial or European Region with the Creator and Submitter roles, or the Security Lead role. To review results, you must have the Reviewer role. The United States Federal Region is not supported. If you do not have an account, on the Sign in page in the Veracode Platform, select Sign up for a free 14-day trial.
- If you are behind a firewall, ensure the required IP addresses are on your allowlist.
- For an analysis of an API, ensure you have the URL where your API specification file is located. You can also provide the URL and the API specification file through a webhook. The file must be OpenAPI 2.0 (Swagger) or 3.0 in JSON or YAML. HAR files are not supported.
Access DAST Essentials
- Sign in to the Veracode Platform. If you sign in with a free trial account, the Target list page opens.
- Select Scans & Analysis > DAST Essentials. The Target list page opens.
Create a target
-
On the Target list page, select ADD TARGET.
-
Select A web application or An API, then select Next.
-
On the Provide details step, provide the following information:
- Enter a meaningful name for the target.
- Select the protocol to access the target URL.
- Enter the URL to access the web application or API server.
- To specify which users have visibility to this target and the results, select one or more teams. If your account has the Security Lead role, selecting a team is optional.
-
Select Next.
-
If this target is for an API, on the API specification page, enter the URL to the API specification file you want to analyze. Or, enter the URL and the API specification file through a webhook.
-
Select Next.
-
To specify the scope or depth of the scan, select Quick scan or Full scan. The scope defines the default security scanners you want to run.
-
A quick scan takes approximately three to five minutes to complete. It runs only non-invasive scanners and detects basic misconfigurations in your web application or API that a hacker might exploit.
-
A full scan can take 30 minutes or more than 24 hours to complete. It runs all security scanners to mimic the same actions a hacker might take to exploit your web application or API. The scanners only use non-destructive injection code.
-
-
To certify that you have the right to scan the target URL, select the corresponding checkbox.
noteBecause a full scan simulates real-world attacks on the target URL, and these scans can degrade the performance of your web application or API, only scan URLs that you have the right to scan. Otherwise, the hosting provider might notice malicious attacks from Veracode.
-
Select CREATE TARGET. The Target list page opens and your new target is listed.
Run the analysis
-
On the Target list page, select the name of your target.
-
Select RUN ANALYSIS.
-
To monitor the progress, in the ALL ANALYSIS RUNS section, check the STATE column. An active analysis shows an animated bar and a completed analysis shows a solid color that reflects the severity of the most critical findings.
-
To open the Analysis run page, in the URL column, select the URL.
On the Analysis run page, the SCAN INFORMATION section shows the estimated remaining time to complete the analysis, and the number of attack requests sent by the scanners. During the scan, the Duration field shows
Scanning....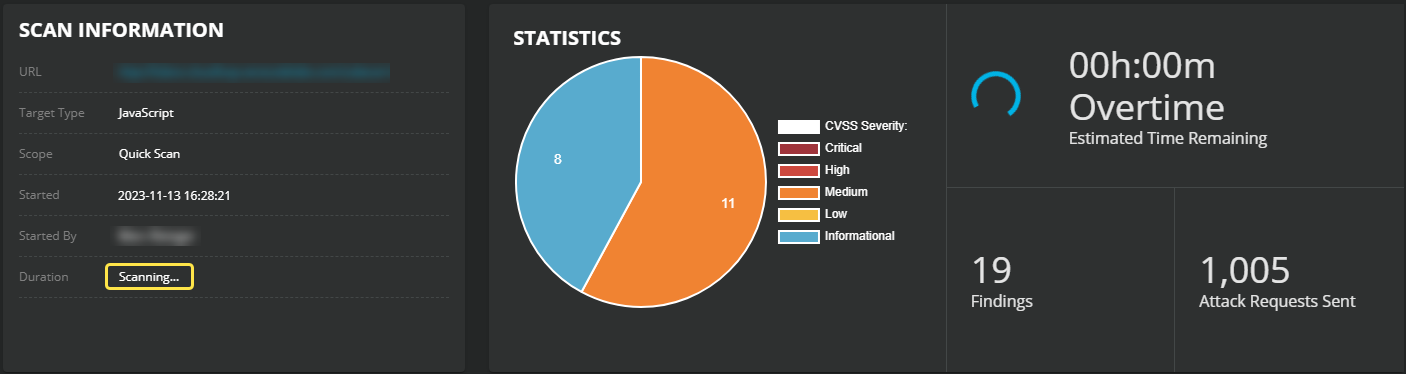
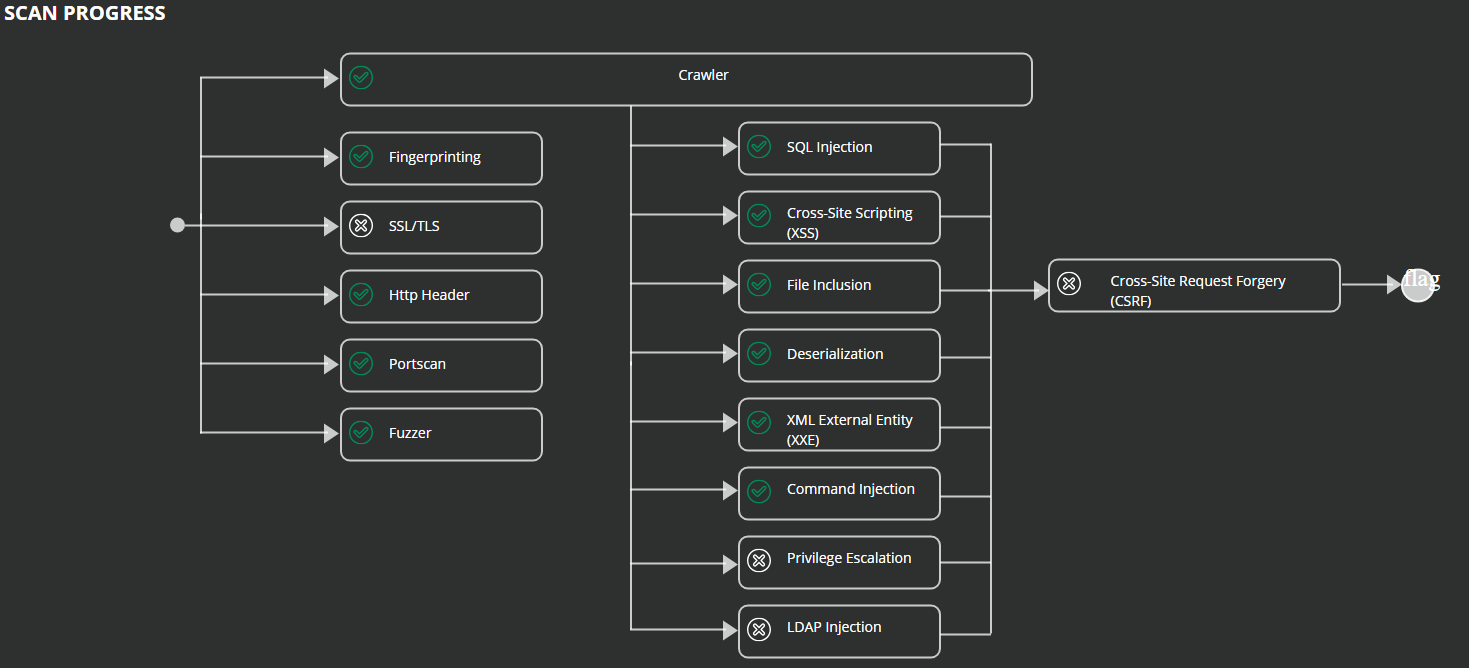
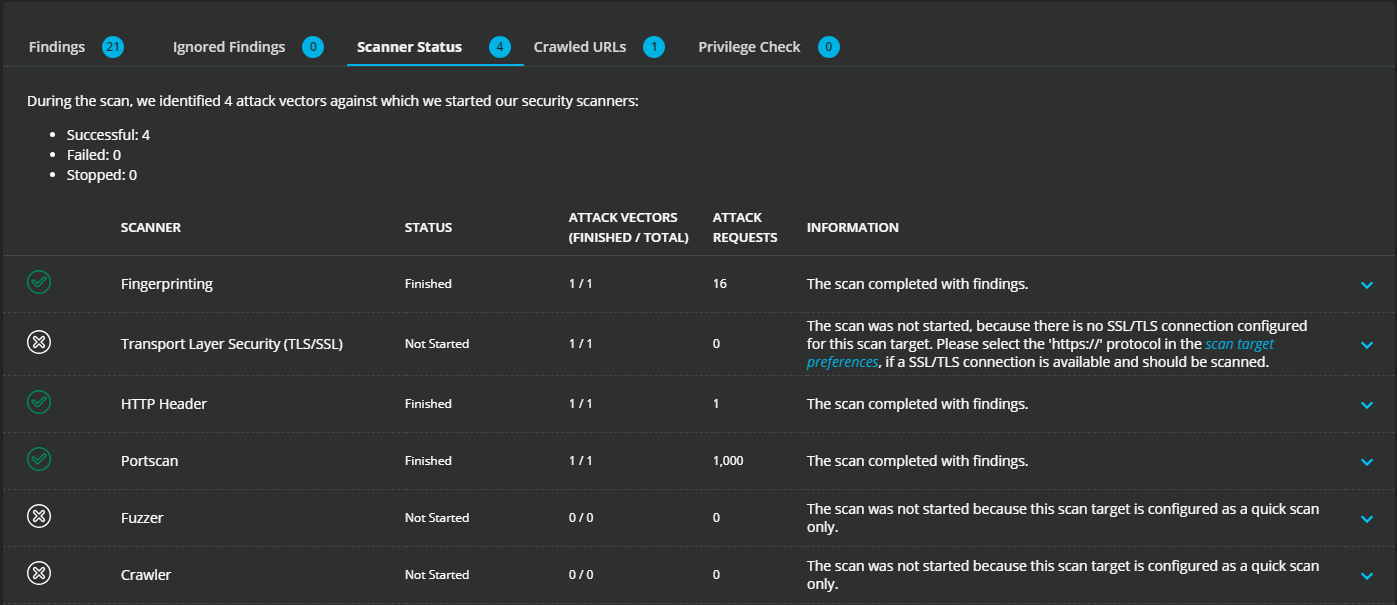
In the SCAN PROGRESS section, the flowchart tracks the status, such as started, not started, or finished, of each scanner and indicates any errors. For help with scanner errors, see troubleshooting.
-
To see more details about each scanner, under the SCAN PROGRESS section, select the Scanner Status tab.
Review the results
The results are available in real-time during the analysis. You can see the findings as the scanners discover them and, for a web application, the crawled URLs for each page.
-
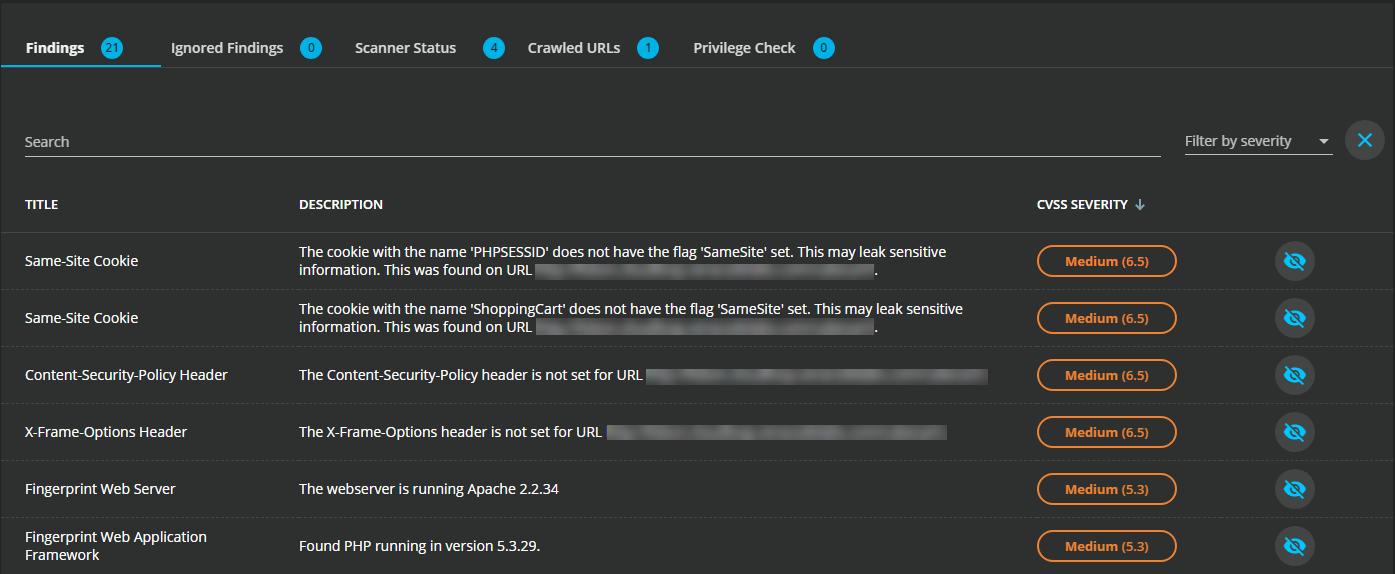
To review the findings, under the SCAN PROGRESS section, select the Findings tab. This tab shows the vulnerability type, a brief summary about how the scanners discovered it, and its severity, which is based on the Common Vulnerability Scoring System (CVSS).
-
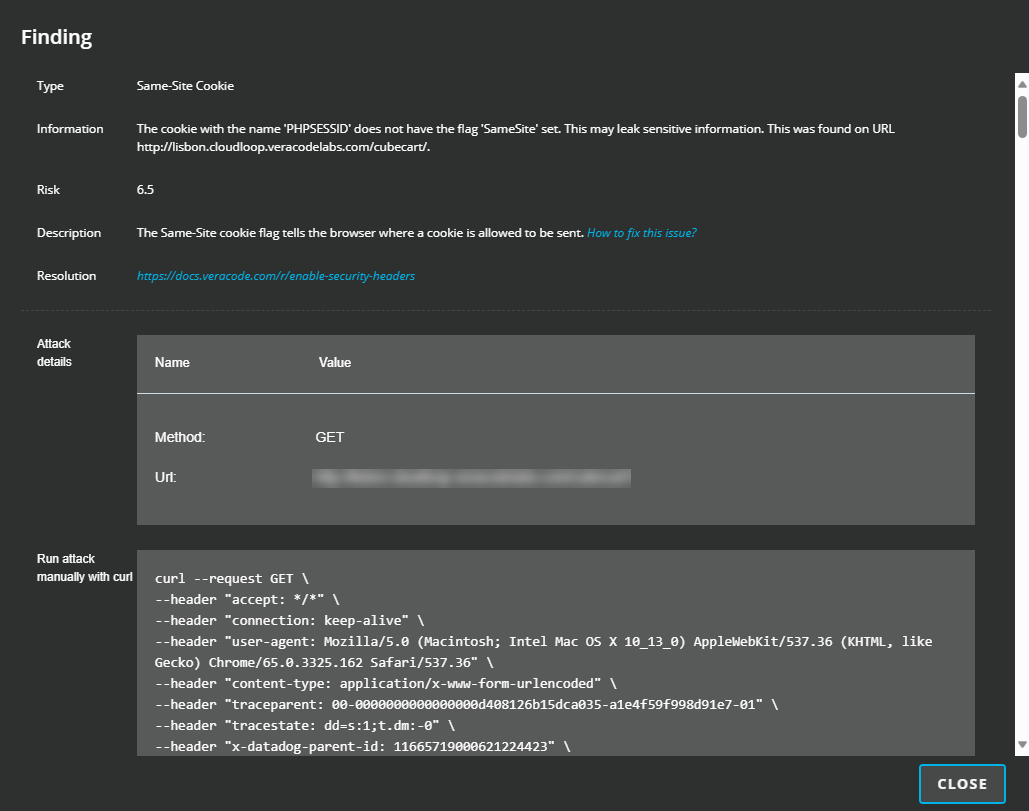
To see more details about a finding, select it to open the Finding window. This window provides links to remediation guidance, including information about the attack requests, such as the payloads the scanners used to exploit the vulnerability. It also provides a curl command that you can use to replicate the attack.
-
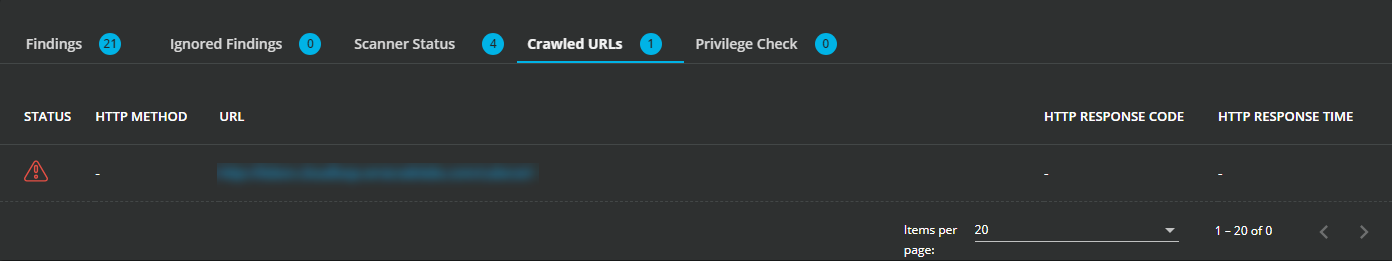
To see a list of all crawled URLs, select the Crawled URLs tab. By default, the scanners do not follow any redirects. For more information about the crawlers, see DAST Essentials URL configuration. In the following example, in the STATUS column, the red triangle indicates discovered findings.
-
To check if the analysis is complete, in the SCAN INFORMATION section, the Duration field changes from
Scanning...to the total analysis time.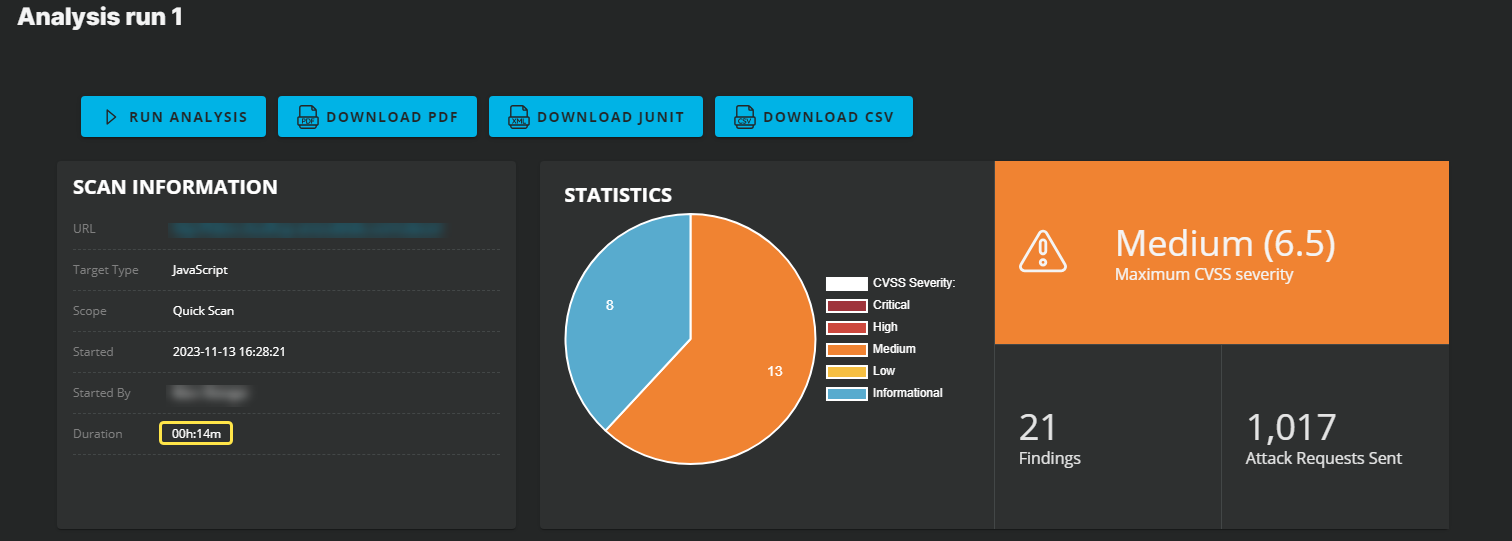
You are done! You have completed your first dynamic analysis and reviewed the results with DAST Essentials.
Optional: Configure the target
After you create a target, you can configure various settings on the Configure target page.
-
On the Target list page, select the name of your target.
-
To open the Configure target page, select CONFIGURE.
-
Select a tab to access the configuration options. For example:
- To automate your analyses, you can schedule them. Select the Schedules tab, then set a schedule for an analysis to run daily, weekly, or monthly.
- To configure authentication methods for crawling a web application or API, select the Authentication tab.
- To add dynamic analysis to a CI/CD pipeline through a webhook, select the Integrations tab. Then, select your provider, such as Jenkins, copy the script, and add it to a step in your pipeline. Veracode recommends that you add the analysis to a pre-production, staging, or test pipeline.
Next steps
- Learn more about the scanners and how you can increase scanning speed.
- Learn about mitigating findings.
- Learn more about the integrations.
- Read the FAQs for answers to common questions about DAST Essentials.